Uncover hidden vulnerabilities and fortify your web applications with precision-driven penetration testing by our elite offensive security experts.
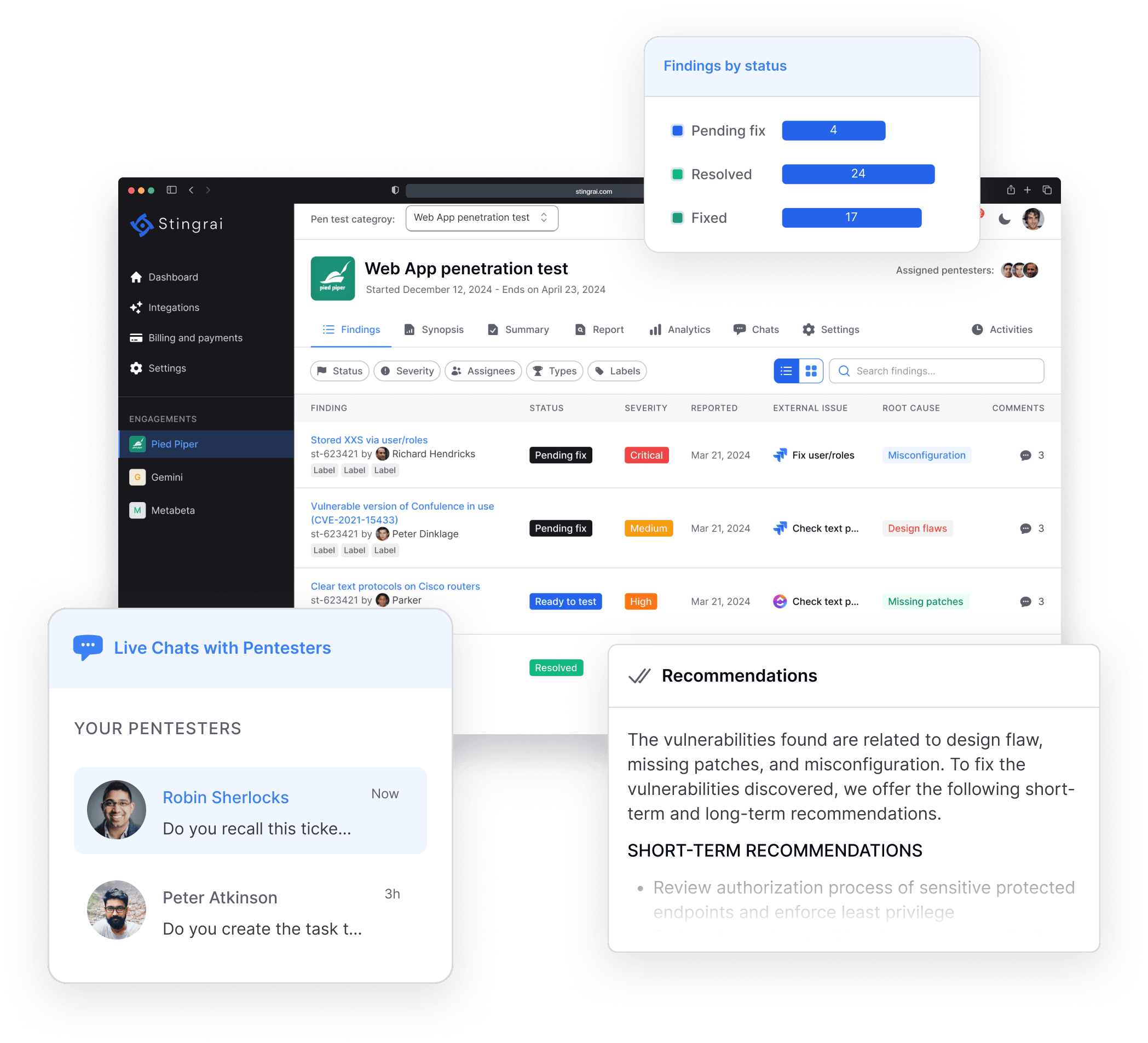
Led by expert white-hat hackers and delivered through our Penetration Testing as a Service (PTaaS) platform.

Web application penetration testing helps identify critical vulnerabilities that could lead to website defacement, data breaches, and loss of customer trust.
Our penetration testing team will conduct thorough assessments and provide you with a detailed report that includes actionable insights and recommendations to fix the gaps.
By completing this assessment, you'll significantly reduce your risk of:
Website defacement
Unauthorized access to user accounts
Exploitation of business logic flaws
Sensitive data exposure (e.g. PII, payment details)
Abuse of authentication or session mechanisms

Black Box
Simulates an external attacker with no prior knowledge of the target environment. Penetration testers have no access to internal systems, credentials, or architecture, allowing for a realistic assessment of perimeter defenses and how easily an attacker could gain initial access or exploit externally exposed vulnerabilities.

Gray Box
Simulates an insider threat with limited knowledge or access such as user-level credentials or network topology simulating an attacker with some level of internal insight. This approach helps uncover vulnerabilities that may be missed in black box testing, especially those tied to authenticated users or partially exposed systems.

White Box
Performed with full access to internal documentation, configurations, source code, and credentials. This deep-dive approach enables a comprehensive security review, allowing for the identification of logic flaws, insecure code, misconfigurations, and complex attack paths that would be invisible in black or gray box assessments.

Our web application security testing helps you identify and address vulnerabilities before they can be exploited by real cyber attacks. By detecting critical risks early, we enable you to mitigate potential threats and safeguard your business from harmful security breaches.
.14530694.svg)
We align our penetration testing with top industry standards, including PTES, OWASP Testing Guide v4.0, OWASP API Security Project, and NIST SP800-115. This ensures that your security measures meet key regulatory compliance frameworks such as SOC2, PCI DSS, ISO27001 etc.
.14530694.svg)
Investing in web application penetration testing is a cost-effective strategy compared to the high expenses associated with data breaches and successful cyber attacks. By proactively addressing vulnerabilities, you can avoid significant financial losses and reputational damage, ultimately saving valuable resources.
.14530694.svg)
Through detailed simulations of real-world attack scenarios, our penetration testing enhances your application's security. This includes testing for web application vulnerabilities such as XSS, SQLi, Access Control, Misconfiguration and more. The result is a robust and resilient security posture that significantly reduces your risk profile.
.14530694.svg)
Innovative PTaaS Platform
Our Penetration Testing as a Service (PTaaS) model provides continuous, on-demand security testing, giving you real-time insights and proactive threat management. We focus on delivering measurable improvements, backed by detailed reports and recommendations.
Proven Track Record
We have a history of successfully securing businesses of all sizes, from startups to Fortune 500 companies. Don’t just take our word for it, read verified customer reviews about our work on Clutch.co.
Client-Centric Approach
We prioritize your needs and work closely with you throughout the process, offering clear communication, regular updates, and ongoing support.
Simulate Real Threats
At Stingrai, we don’t just run tests—we simulate real-world hacking scenarios to expose vulnerabilities before malicious actors can exploit them. By replicating the tactics, techniques, and procedures of real hackers, we identify critical weaknesses and show you exactly what needs to be fixed.
Expert Remediation Support
Stingrai offers detailed remediation steps along with free on-call support, ensuring our clients receive expert guidance to efficiently fix vulnerabilities and strengthen their security.
Accessible to All
We believe advanced security should be accessible to all. That’s why Stingrai offers competitive pricing without compromising on quality. Protect your organization with top-tier security assessments tailored to your budget.
Simulate real-world attacks with the expertise of our elite white-hat hackers. We identify vulnerabilities before they can be exploited, providing clear guidance on how to fix them through our cutting-edge platform, all at competitive pricing.

