Protect your physical perimeter through real-world intrusion attempts to test badge cloning, tailgating, and unauthorized access. Identify gaps in physical controls, staff awareness, and building access security.
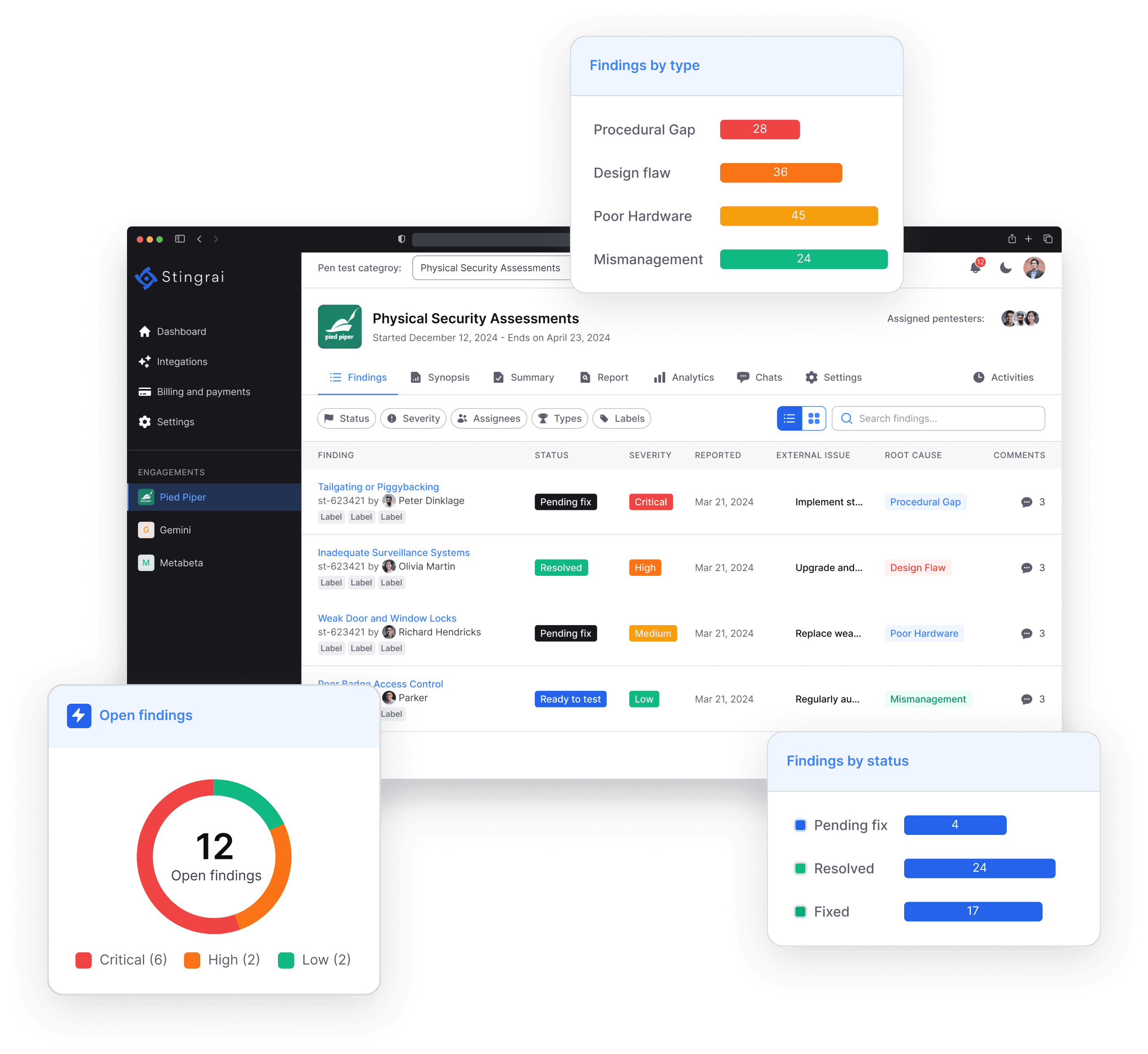
Led by our expert white-hat hackers and delivered through our Penetration Testing as a Service (PTaaS) platform.

Our Physical Security Assessment is designed to help you identify and address any vulnerabilities within your physical security perimeter. By simulating real-world attacks, we attempt to compromise your security using advanced techniques like RFID Cloning, Tailgating, and Social Engineering, focusing on sample locations of your choice.
Reduce the risk of external adversaries gaining access to your internal network
Avoid physical security bypass through access card cloning, lockpicking and social engineering
Lower the chances of keystroke logger attacks that can compromise sensitive information
Identify and address physical security risks with real-world attack simulations

Proactive Threat Detection
Identify potential loopholes in your physical security before adversaries can exploit them.

Tailored Security Solutions
Customized assessment based on your selected locations, ensuring targeted and relevant testing.

Expert Recommendations
Receive actionable advice on how to strengthen your physical defenses.



RFID Cloning
Attempting to duplicate access cards to bypass security controls.

Tailgating
Testing the effectiveness of entry protocols by trying to gain unauthorized access.

Social Engineering
Simulating social engineering attacks to exploit human factors in your security measures.
Innovative PTaaS Platform
Our Penetration Testing as a Service (PTaaS) model provides continuous, on-demand security testing, giving you real-time insights and proactive threat management. We focus on delivering measurable improvements, backed by detailed reports and recommendations.
Proven Track Record
We have a history of successfully securing businesses of all sizes, from startups to Fortune 500 companies. Don’t just take our word for it, read verified customer reviews about our work on Clutch.co.
Client-Centric Approach
We prioritize your needs and work closely with you throughout the process, offering clear communication, regular updates, and ongoing support.
Simulate Real Threats
At Stingrai, we don’t just run tests—we simulate real-world hacking scenarios to expose vulnerabilities before malicious actors can exploit them. By replicating the tactics, techniques, and procedures of real hackers, we identify critical weaknesses and show you exactly what needs to be fixed.
Expert Remediation Support
Stingrai offers detailed remediation steps along with free on-call support, ensuring our clients receive expert guidance to efficiently fix vulnerabilities and strengthen their security.
Accessible to All
We believe advanced security should be accessible to all. That’s why Stingrai offers competitive pricing without compromising on quality. Protect your organization with top-tier security solutions tailored to your budget.
Simulate real-world attacks with the expertise of our elite white-hat hackers. We identify vulnerabilities before they can be exploited, providing clear guidance on how to fix them through our cutting-edge platform, all at competitive pricing.

