Comprehensive Penetration testing as a service (PTaaS) platform and a team of elite white-hat-hackers to protect your digital assets.
Led by our expert white-hat hackers and delivered through our Penetration Testing as a Service (PTaaS) platform.
Adversary Simulation is a security testing approach where we mimic the tactics, techniques, and procedures of real-world attackers to assess an organization’s defenses. Unlike traditional testing, Adversary Simulation is designed to replicate the actions of a skilled hacker, providing a realistic evaluation of your security posture.
Through penetration testing, we simulate potential attacks on your systems, attempting to exploit vulnerabilities just as a malicious actor would. This proactive approach helps organizations identify and address security gaps before they can be exploited by cyber criminals.
By uncovering and fixing these vulnerabilities, Stingrai can protect your organization from:
Data breaches
Legal liabilities
Loss of brand reputation
Significant financial losses


Start your Pentest
Begin by filling out our online form to request a quote tailored to your specific cybersecurity needs.
Receive & Sign SOW
After reviewing your requirements, we’ll send you a customized quote along with a Statement of Work (SOW). This document outlines the scope, deliverables, and timelines. Once you’re satisfied, simply sign the SOW to proceed.
Onboard to the Portal
Upon signing the SOW, you’ll receive an invitation to join our secure client portal. This portal will serve as your command center throughout the testing process, giving you control and visibility into every step.
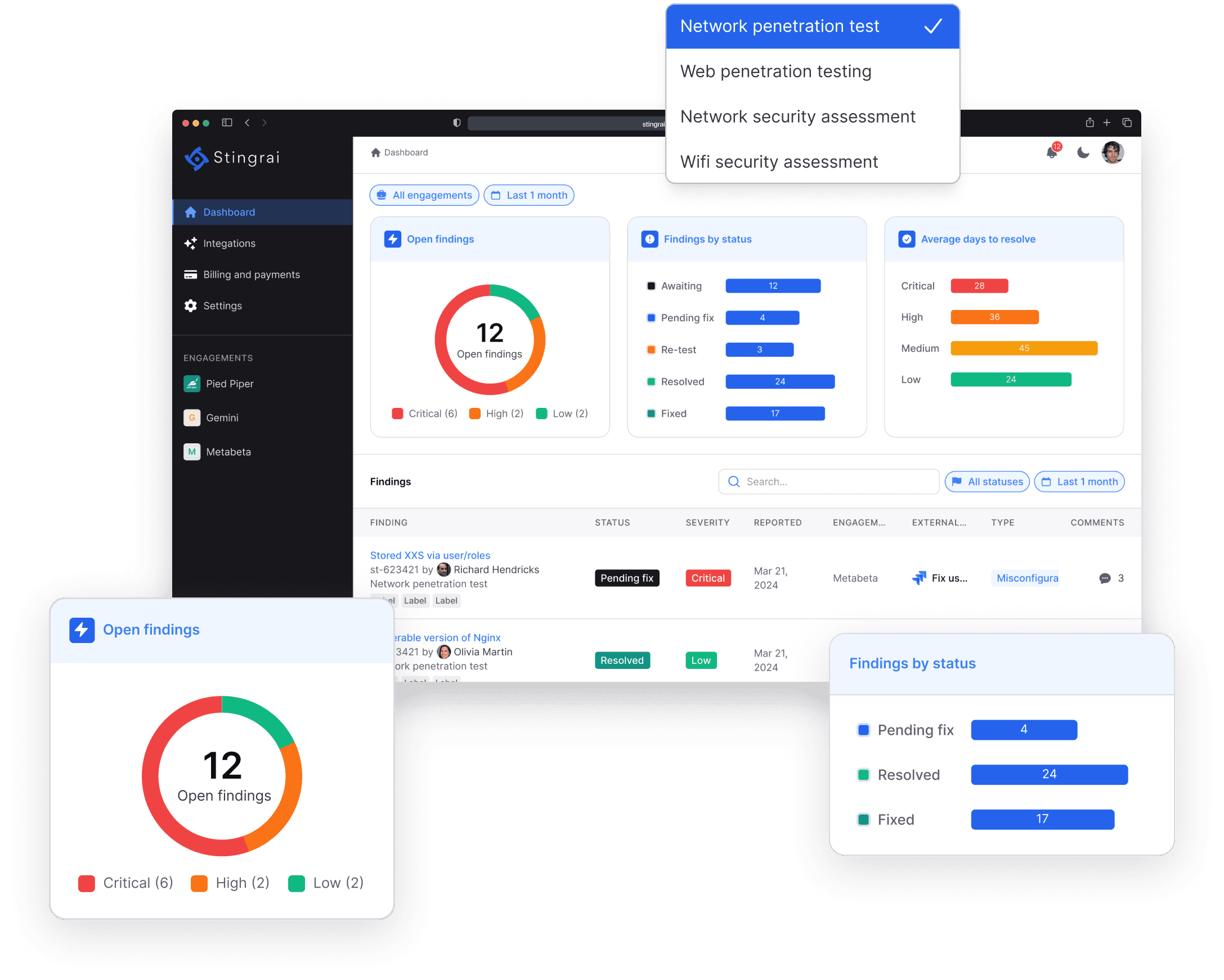
View Live Findings
As our certified ethical hackers begin testing your systems, you’ll see live findings directly in the portal. This real-time insight allows you to monitor vulnerabilities as they’re discovered, giving you immediate visibility into potential risks.
Integrate with Your Ticketing System
Our platform offers seamless integration with your existing ticketing system. This means you can automatically forward findings to development teams, ensuring swift action and tracking without disrupting your current workflows.
Request Retests
Once your team has addressed the vulnerabilities, you can easily request a retest through the portal. Our experts will verify that the issues have been resolved, providing you with peace of mind that your systems are secure.
Communicate via Live Chat
Stay connected with our hackers in real-time using our live chat feature. Whether you need clarification on a finding or have questions during the retest, our team is always available to assist you.
Customize and Download Your Reports
Our platform allows you to select which sections to include in your final report, ensuring that only the relevant information is shared externally. Download your customized report with confidence, knowing that sensitive data remains protected.
Innovative PTaaS Platform
Our Penetration Testing as a Service (PTaaS) model provides continuous, on-demand security testing, giving you real-time insights and proactive threat management. We focus on delivering measurable improvements, backed by detailed reports and recommendations.
Proven Track Record
We have a history of successfully securing businesses of all sizes, from startups to Fortune 500 companies. Our clients trust us to deliver results that make a tangible difference.
Client-Centric Approach
We prioritize your needs and work closely with you throughout the process, offering clear communication, regular updates, and ongoing support.
Simulate Real Threats
At Stingrai, we don’t just run tests—we simulate real-world hacking scenarios to expose vulnerabilities before malicious actors can exploit them. By replicating the tactics, techniques, and procedures of real hackers, we identify critical weaknesses and show you exactly what needs fixing.
Expert Remediation Support
Stingrai offers detailed remediation steps along with free on-call support, ensuring our clients receive expert guidance to efficiently fix vulnerabilities and strengthen their security.
Accessible to All
We believe advanced security should be accessible to all. That’s why Stingrai offers competitive pricing without compromising on quality. Protect your organization with top-tier security solutions tailored to your budget.
Continuously simulate real-world attacks with the expertise of our elite white-hat hackers. We identify vulnerabilities before they can be exploited, providing clear guidance on how to fix them through our cutting-edge platform, all at competitive pricing.

